If you are running the Starter VM (autoconfiguration mode), no further action is needed and you may proceed with deploying capabilities into your newly deployed Defused VM.
However, if you are running a non-autoconfig VM (e.g. for static networks), proceed with the network configuration section below.
Now that the server is running, we'll set up networking inside the decoy server image. The default credentials are
Run our networking script inside the decoy server image to auto-setup networking:
Check what IP address was set up for your decoy server. It will look something like the following:
This is the address where you can access your decoy server's management interface. Before logging into the GUI, reboot the decoy server to ensure it has configured correctly:
Your decoy server networking is now set up. It may a minute to reboot.
This link contains an additional installer script to get up and running as fast as possible.
First, ensure you have the necessary KVM packages on the host machine.
- In Fedora/CentOs:
yum -y install virt-viewer virt-manager qemu-kvm bridge-utils net-tools virt-install libvirt
- In Debian/Ubuntu:
apt install -y virt-viewer virt-manager qemu-kvm bridge-utils net-tools virtinst libvirt-daemon-system
Installing the Server
Once all necessary KVM packages are installed onto the host, copy/move the decoy server image (.qcow2) and your install script (.sh) into the following directory:
cp aves-freemium.* /var/lib/libvirt/images/
Now, jump into /var/lib/libvirt/images and edit the decoy server's ethernet interface according to your host machine interface:
cd /var/lib/libvirt/images
ip addr #your ethernet interface should start with "eth*", "eno*", "ens*", "enp*" or similar
sudo nano aves-freemium.sh # edit ethernet interfaces here
When editing aves-freemium.sh, change MANAGEMENT_INTERFACE and DECOY_INTERFACE according to your ethernet interface(s) (e.g. enp2s0).
Starting the Decoy Server
In /var/lib/libvirt/images on the host machine:
chmod a+x aves-freemium.sh
sudo ./aves-freemium.sh
Your decoy server should now install and start.
If you're using a graphical desktop, the decoy server (KVM) window should pop up automatically after executing aves-freemium.sh. If not:
There should be a login prompt when the server has successfully started. Use the user/password combination
XXXXXXXXXX
Sign up to view the password
when logging in. Remember to change this password after your first login.
user: [decoy-server-user], password: [decoy-server-password]
sudo su [password]
Networking Setup
Now, we'll set up networking inside the decoy server image.
Run our networking script inside the decoy server image to auto-setup networking:
sudo /opt/aves/avestool -d #this generates /opt/aves/aves.conf
Check what IP address was set up for your decoy server. It will look something like the following:
ip a #check the IP address of the GUI for access to it
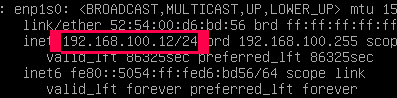
This is the address where you can access your decoy server's management interface. We need to visit soon it to connect your decoy server with your cloud management. Finally, reboot the decoy server to ensure it has configured correctly:
sudo reboot #Restart KVM
Your decoy server networking is now set up. It may take a couple minutes to reboot. You can now jump into the Logging into the Local Server section.
Defused VM - Hyper-V
Prerequisites
This guide assumes you have the Hyper-V Manager installed.
Create the Decoy Server Virtual Machine
Open Hyper-V Manager and create a new virtual machine with the following settings:
-
Specify Name and Location
Give your virtual machine a name of choosing. (e.g. DefusedVM1)
-
Specify Generation
Select Generation 1.
-
Assign Memory
We suggest a minimum of 2048MB for the VM. You can keep dynamic memory checked.
-
Connect Virtual Hard Disk
Select “Use an existing virtual hard disk” and set it to the Defused virtual hard disk file provided to you.
-
Finish
You can now click “Finish” and complete the install.
Before Powering on Your Defused Server
There’s a few extra configurations needed before powering on the Defused Server.
Networking – Test Setup
For testing purposes, a simple NAT network setup will be sufficient. In the Hyper-V
Manager, go to “Virtual Switch Manager” and create a new External virtual switch.
Then, connect this to your network adapter of choice.
This setup will make both the management UI and the decoys available in the same
network as your host machine (i.e. the machine running your Hyper-V Manager.)
Networking – Production Setup
For production deployments, we highly recommend setting up the decoy interface
and the management interface into separate network. For Defused customers, we
offer complementary networking help over Zoom - please consult with us for
suggestions how to set your decoys up in the most safe manner.
Boot Order
Set “IDE” to be on the top of the boot order list.
Connecting your Defused Server to the network
If you did not already have a ready virtual network switch when creating the virtual
machine, right click on your Defused VM on the main screen of Hyper-V Manager
and click “Settings.”
Under the list of hardware, find “Network Adapter” and change the virtual switch
from “not connected” to the new virtual switch created in the above step.
Before clicking “Apply”, make sure to also enable MAC address spoofing under the
“Advanced Features” tab (see image below):
Click apply and your networking setup will be done.
You can now power on the VM.
Starting the Decoy Server
Now that the server is running, we'll set up networking inside the decoy server image. Log in with your supplied credentials:
user: [decoy-server-user], password: [decoy-server-password]
sudo su [password]
Run our networking script inside the decoy server image to auto-setup networking:
/opt/aves/avestool -d
Check what IP address was set up for your decoy server. It will look something like the following:

This is the address where you can access your decoy server's management interface. Before logging into the GUI, reboot the decoy server to ensure it has configured correctly:
Your decoy server networking is now set up. It may a minute to reboot.
You can now jump over to the section Logging into the Local Server.